A UK cybersecurity researcher founds how to halt the spreading of one of the most dangerous malwares of the last years. The method? Just spending 10.60 dollars in registering a very long domain which is consulted by the Wannacry ransomware
During the last hours, a ransomware called WannaCry affected lots of world wide organizations like Telefonica, FedEx or the UK’s National Health Service (NHS), where hospital computers started showing a ransom message demanding $300 worth of bitcoin.
Now, an “accidental hero” has interrupted the global spread of the ransomware, just by spending a few dollars registering a domain name that the malware makes a request to.
This man, apparently a UK cybersecurity researcher who tweets as @malwaretechblog, found that the switch was hardcoded within the ransomware “in case the creator wanted to stop it spreading”. This was made through a very long domain name that the malware had to connect to (very similar to looking up any website). If the connection is ok, and it shows a live domain, the ‘kill switch’ works, it shuts itself down immediately, and the spreading of the ransomware is halted.
In the following tweet, Warren Mercer (technical security Leader at Cisco), confirmed that infections for WannaCry/WanaDecrpt0r are down due to the discovery of @ MalwareTechBlog
Infections for WannaCry/WanaDecrpt0r are down due to @MalwareTechBlog registering initial C2 domain leading to kill-switch #AccidentalHero
— Warren Mercer (@SecurityBeard) May 12, 2017
The domain is a dot-com address, formed by a long string of gobbledygook letters and numbers, ‘iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com’. According to TheDailyBeast, @MalwareTechBlog saw that the domain wasn’t registered and decided to purchase it at NameCheap.com for just 10.69 dollars. Then, he pointed it at a ‘sinkhole’ server in California, just with the intention of collecting information on the malware. Suddenly, he saw thousands of connections per second.
Cisco detected that the connections to ‘iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com’ started at 07:24 UTC on Friday 12 May, with a peak nearly 10 hours later. You can see the evolution on the following chart:
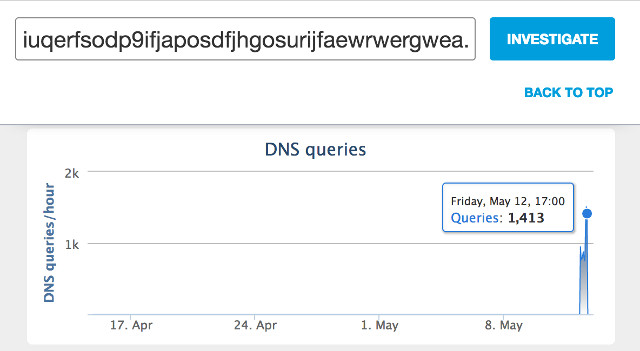
However, @MalwareTechBlog warns about a new coming thread. “There’s a very likely chance that they’re going to unveil a new version of the ransomware to start it again. If people don’t patch their computers it will happen again”, he claimed.
According to Cisco, users must ensure that all their systems based on Microsoft Windows are fully patched. At least , they encourage to apply Microsoft bulletin MS17-010. And any organization with the SMB service publicly accessible via internet (ports 139, 445) should immediately block inbound traffic. Apart to this two recommendations, companies should block all the connections to TOR on network.
The guy is reporting all the finds:
IP addresses from our sinkhole have been sent to FBI and ShadowServer so affected organisations should get a notification soon. patch ASAP.
— MalwareTech (@MalwareTechBlog) May 13, 2017
So long as the domain isn't revoked, this particular strain will no longer cause harm, but patch your systems ASAP as they will try again.
— MalwareTech (@MalwareTechBlog) May 13, 2017
It's very important everyone understands that all they need to do is change some code and start again. Patch your systems now! https://t.co/L4GIPLGKEs
— MalwareTech (@MalwareTechBlog) May 13, 2017
More information at this story of The Guardian and Cisco security blog.

The image used has some rights reserved.